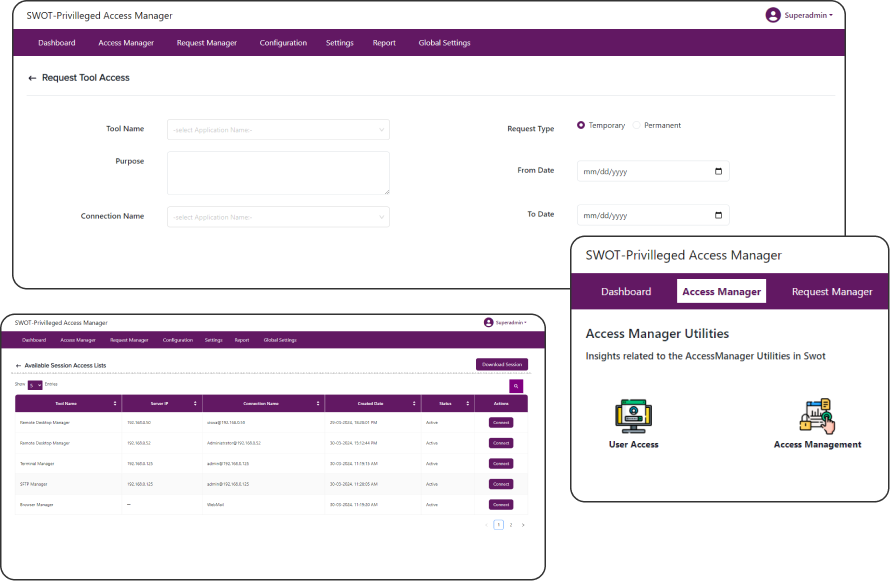
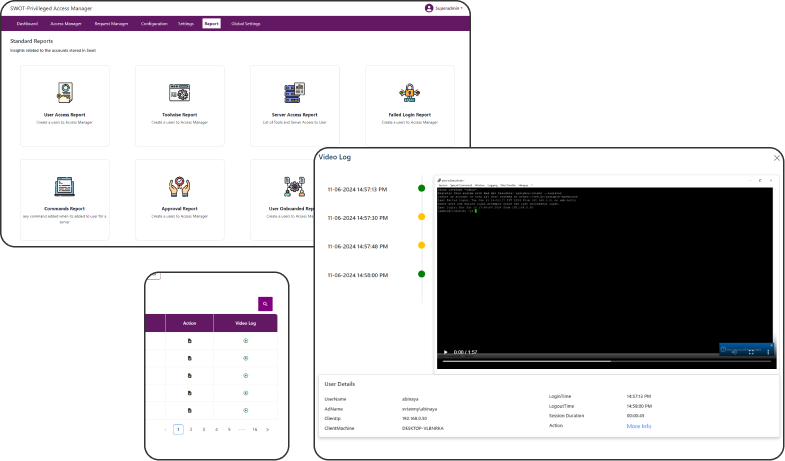
Priviledged Access Management
SWOT Privileged Access Management provides central
control over privileged account credentials and
fortify your privileged data against misuse and emerging
threats.